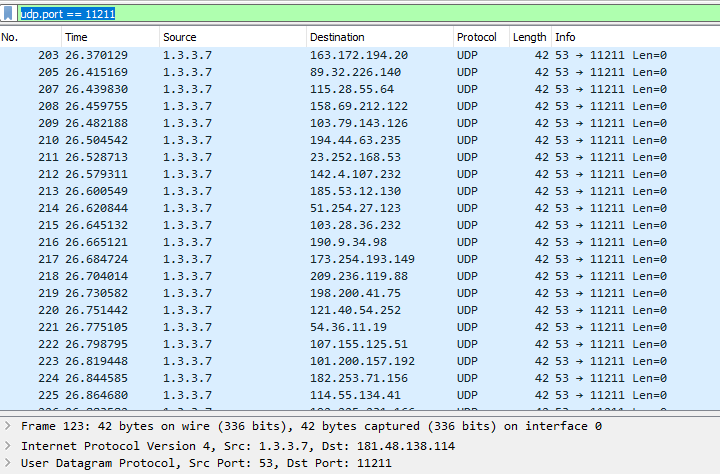
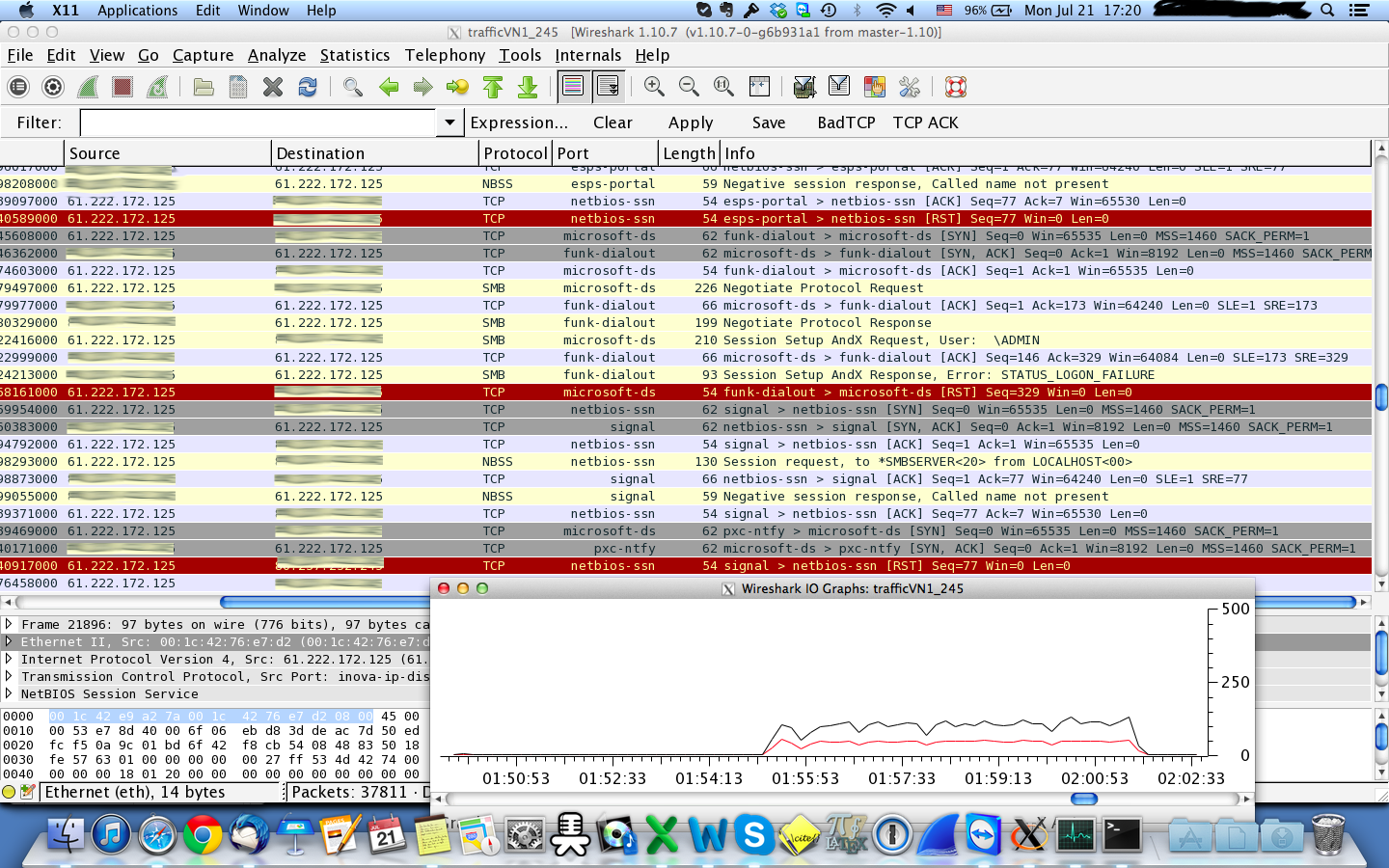
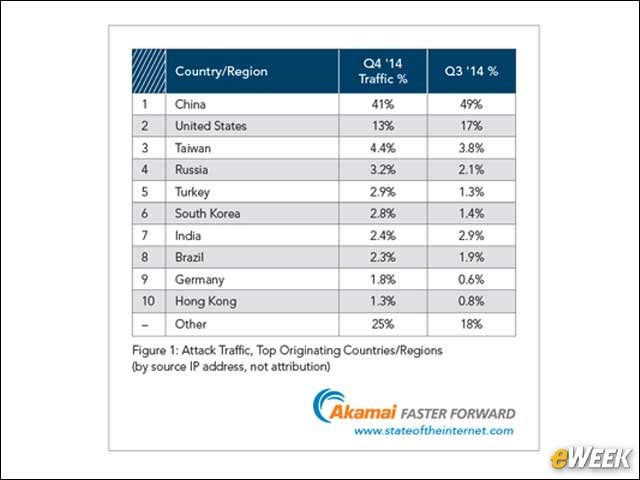
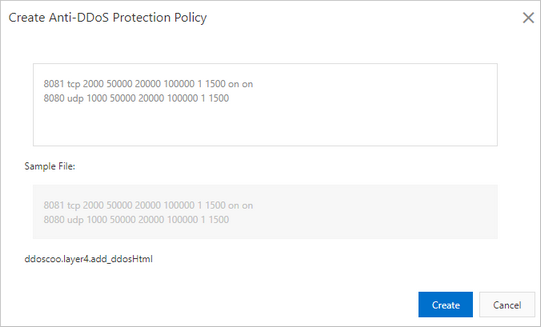
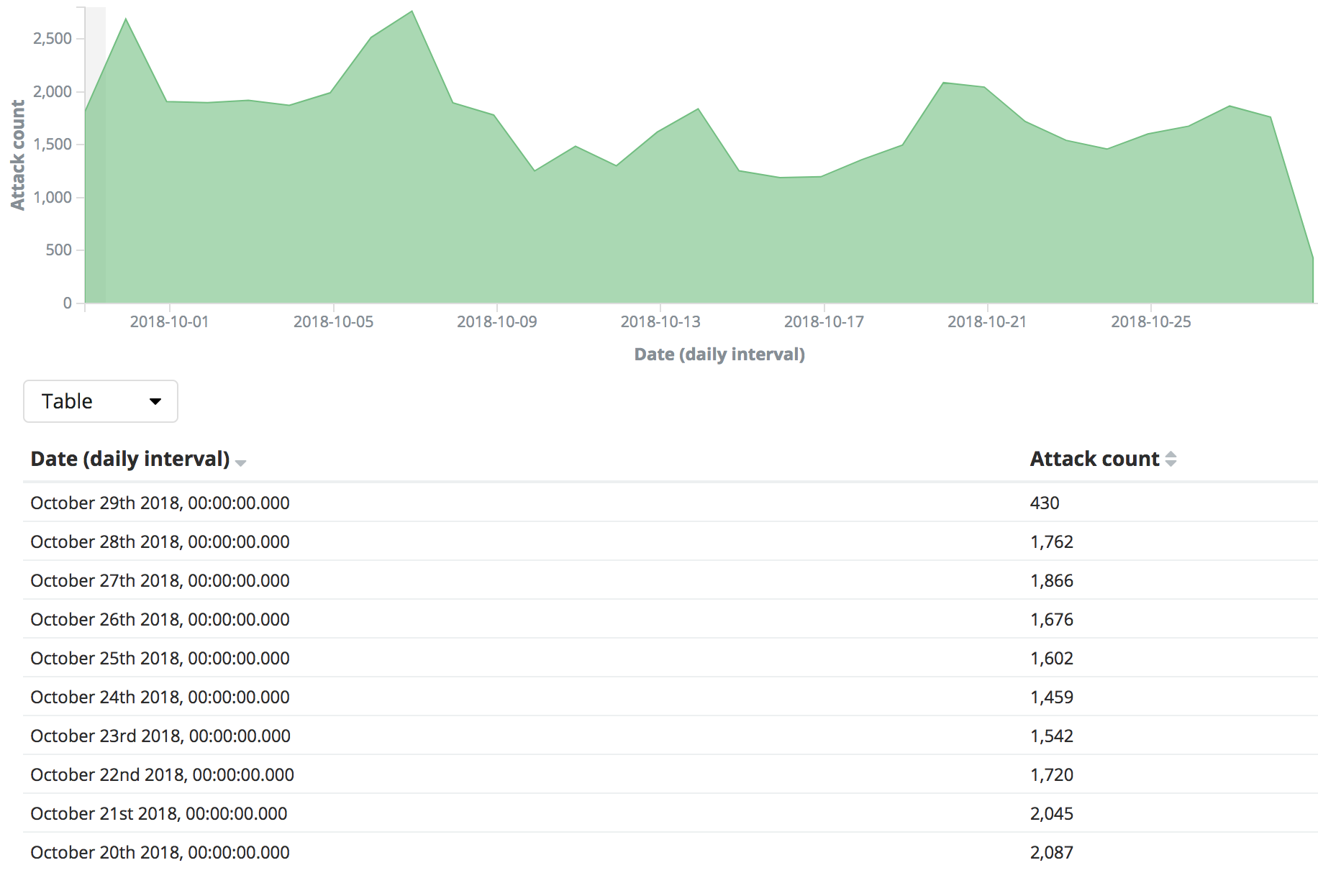
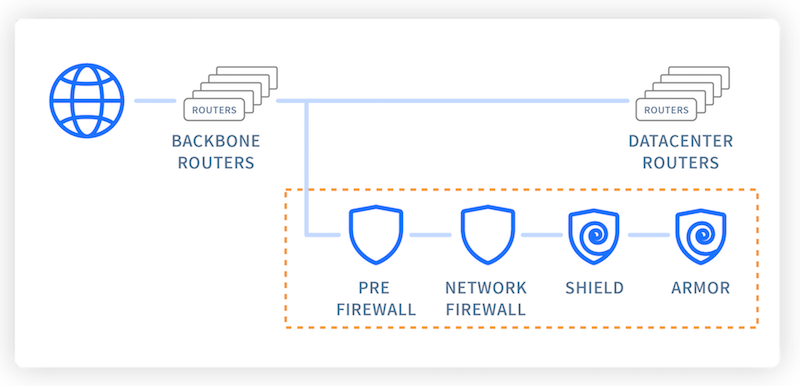
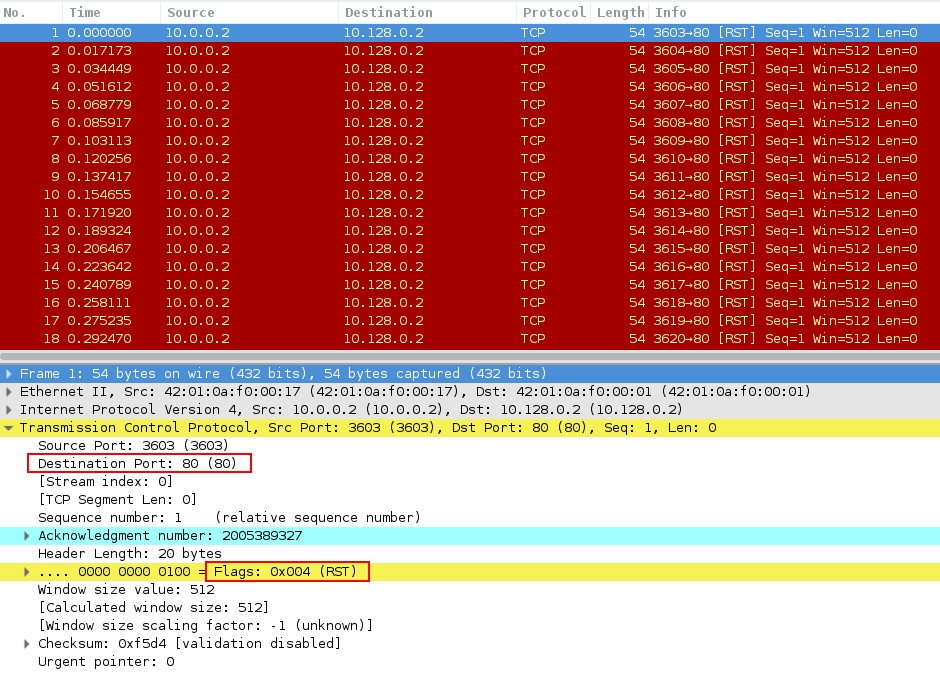
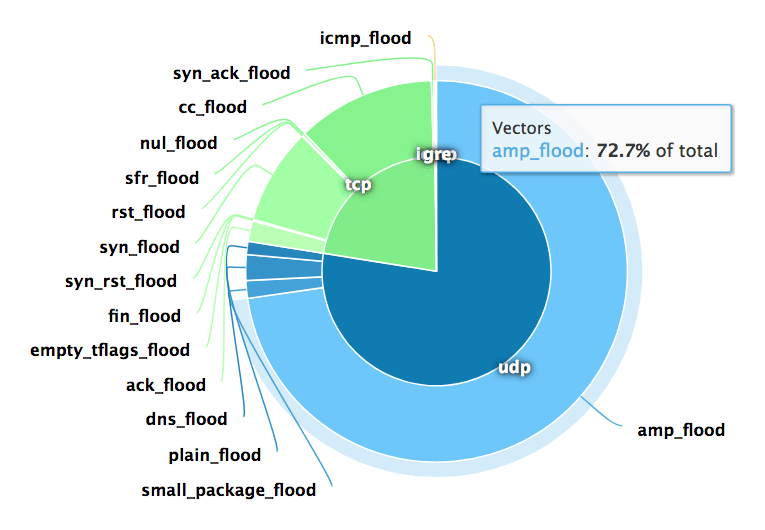
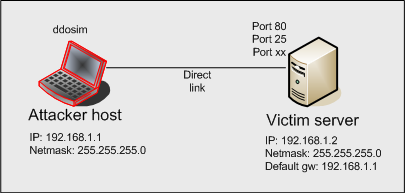
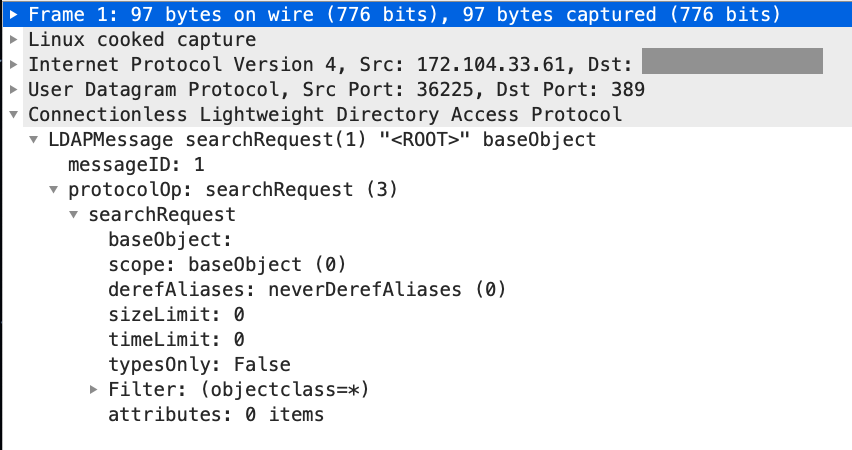
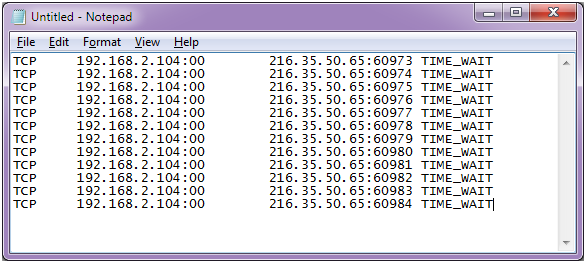
Denial of Service (DoS) attack identification and analyse using sniffing technique in the network environment

What You Should Know About DDoS Incident Response - NSFOCUS, Inc., a global network and cyber security leader, protects enterprises and carriers from advanced cyber attacks.